#include <stdio.h>
#include <Windows.h>
int main(int argc, char** argv)
{
return 0;
}
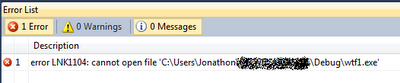
I unintentionally clicked Start Debugging, and much to my surprise,
Really? How did I screw up something so simple? Several seconds later AVG popped up this "Resident Shield Alert":
 |
| Downloader.Agent2.BBLD |
Are you kidding me? So I added a printf...
{
printf("WTF is going on\n");
return 0;
}
Again, threat detected! This time Downloader.Agent2.BAZE. I disabled AVG, built it again (successfully!) and threw the EXE into IDA, worried that I had some impressive virus injecting a trojan into EXEs I build. Nothing out of the ordinary found, just the typical complicated CRT startup code, and my simple main().
I uploaded it to VirusTotal to see if this was just AVG being retarded or what. It had a detection ratio of 8 / 42. Check out that link to see each AV and what they detected it as. It is important to note that AVG picked up the file before it had even finished building (hence the link error) with Resident Shield, but also the finished EXE with a manual scan.
"This is absurd!" I'm thinking. One more try....
int main(int argc, char** argv)
{
printf("WTF is going on\n");
getchar();
printf("This is ridiculous\n");
return 0;
}
Finally, this one built okay and AVG let it alone. Curious, I uploaded this one to VirusTotal too. It was picked up by only 1 / 42 AVs: McAfee-GW-Edition identified it as Heuristic.BehavesLike.Win32.Suspicious.H. Sounds more like Heuristic.WeHaveNoIdea.FlagEverything.H